Rev Rev Rev Writeup - IERAE CTF 2025
My writeup for the Rev/Rev Rev Rev challenge in IERAE CTF 2025
Misc/Rev Rev Rev - Rama
Reverse it.
Initial Thoughts
We are given two files: chal.py, a script that encrypts the flag, and output.txt, the encrypted flag.
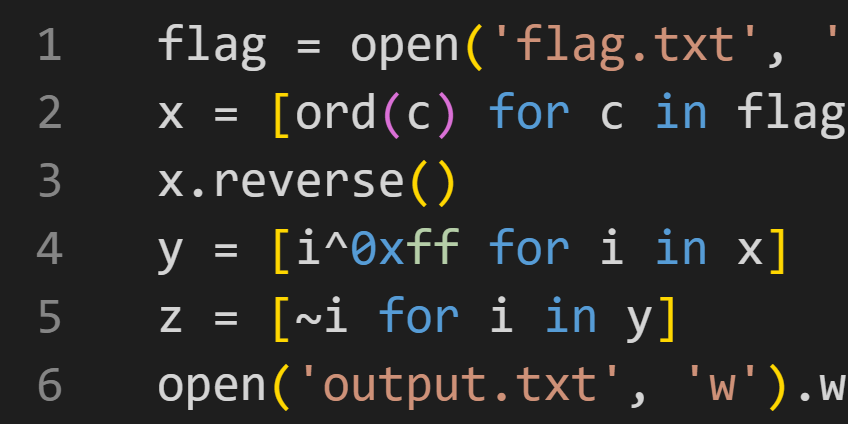
The contents of chal.py.
1
2
3
[-246, -131, -204, -199, -159, -203, -201, -207, -199, -159, -204, -158, -155, -205, -211,
-206, -201, -206, -205, -211, -158, -159, -207, -202, -211, -199, -206, -155, -206, -211,
-204, -200, -200, -200, -203, -208, -159, -199, -133, -187, -191, -174, -187, -183]
The contents of output.txt.
Methodology
For this challenge, all we have to do is reverse the chal.py script. First, let’s figure out what each line does.
1
flag = open('flag.txt', 'r').read()
This line opens the flag and stores it in the flag variable.
1
x = [ord(c) for c in flag]
This converts each character to its corresponding Unicode point value.
1
x.reverse()
This reverses the order of the list of point values.
1
y = [i^0xff for i in x]
This XORs each point value with 0xff, or 255 in decimal.
1
z = [~i for i in y]
This applies the NOT operator to each value, flipping the bits of each integer.
1
open('output.txt', 'w').write(str(z))
This writes the result to output.txt, which we are given.
All we have to do is write a script that does the opposite of each of these lines in the opposite order.
Script
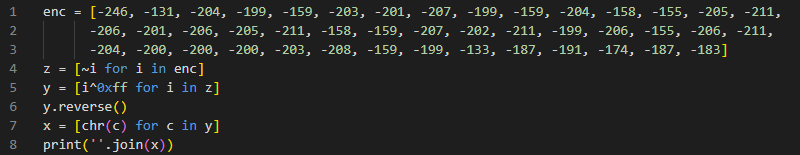
This is my full solution script
1
2
3
enc = [-246, -131, -204, -199, -159, -203, -201, -207, -199, -159, -204, -158, -155, -205,
-211, -206, -201, -206, -205, -211, -158, -159, -207, -202, -211, -199, -206, -155, -206,
-211, -204, -200, -200, -200, -203, -208, -159, -199, -133, -187, -191, -174, -187, -183]
This reverses open('output.txt', 'w').write(str(z)) by storing the contents of output.txt in a variable.
1
z = [~i for i in enc]
This reverses z = [~i for i in y], as the bitwise NOT operator is involutive, meaning applying it twice reverts to the original value.
1
y = [i^0xff for i in z]
This reverses y = [i^0xff for i in x], as the XOR operator, just like the bitwise NOT operator, is involutive.
1
y.reverse()
This reverses x.reverse(), as reversing a list twice reverts it to the original. (Yet another involutive step!)
1
x = [chr(c) for c in y]
This reverses x = [ord(c) for c in flag], as chr(c) converts each item in the list from its Unicode point value to its character representation.
1
print(''.join(x))
Finally, we join the list together, getting our flag.
Solution
The flag is IERAE{9a058884-2e29-61ab-3272-3eb4a9175a94}. This was a pretty simple and fun rev challenge, and I liked how it focused on involutive functions.